Information is your most valuable asset. It’s our passion.
Ready to take control of your information lifecycle? We handle documents for more than 30,000 businesses in North America. Let us help you handle yours.
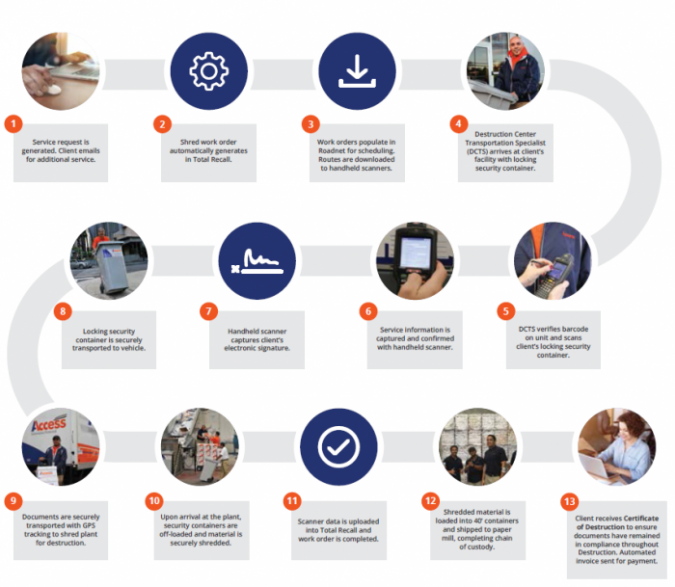
Each Access facility is governed by strict chain-of-custody procedures. Archived documents will have a unique identifier attached, allowing you to track where and when the document is at all time. Whenever an item is retrieved, accessed, or distributed, this information goes into the permanent unique record for that item.